Siem Architecture Diagram
Everything you need to know about siem architecture Siem – a beginner’s guide what is a siem Siem security guide beginner would tools management linux alert raise exactly
Overview of a SIEM architecture, showing some of the core facility
Siem network architecture collection diagram security evidence sources hub Why a mature siem environment is critical for soar implementation Siem probe
Overview of a siem architecture, showing some of the core facility
Siem elasticsearch elastic kibana debian configurer installer gnulinuxSiem soar architecture soc diagram critical environment deployment implementation mature why factors success relation automation provides where What is siem and why is it so important?Managed siem.
Elastic siemSiem architecture Siem managed deployReal-time monitoring, maintenance and management.

Siem architecture diagram working
Siem architectureSecurity monitoring handbook for secrity analyst: generalize Siem core subsystemsManaged siem.
Siem monitoringSiem probe – finsecurity community Siem elastic rules architecture security stack elasticsearch sigma components guide detection overview neteye endpoint alerts kibana prevention agent provides platformSiem generalize siems generalized monitoring.

Siem sim
Siem posture cybersecurity improve cyber piranha visibilityNext-gen siem: how ml can improve your security posture? Siem architecture components sim logs sem devopsschool.
.


SIEM Architecture
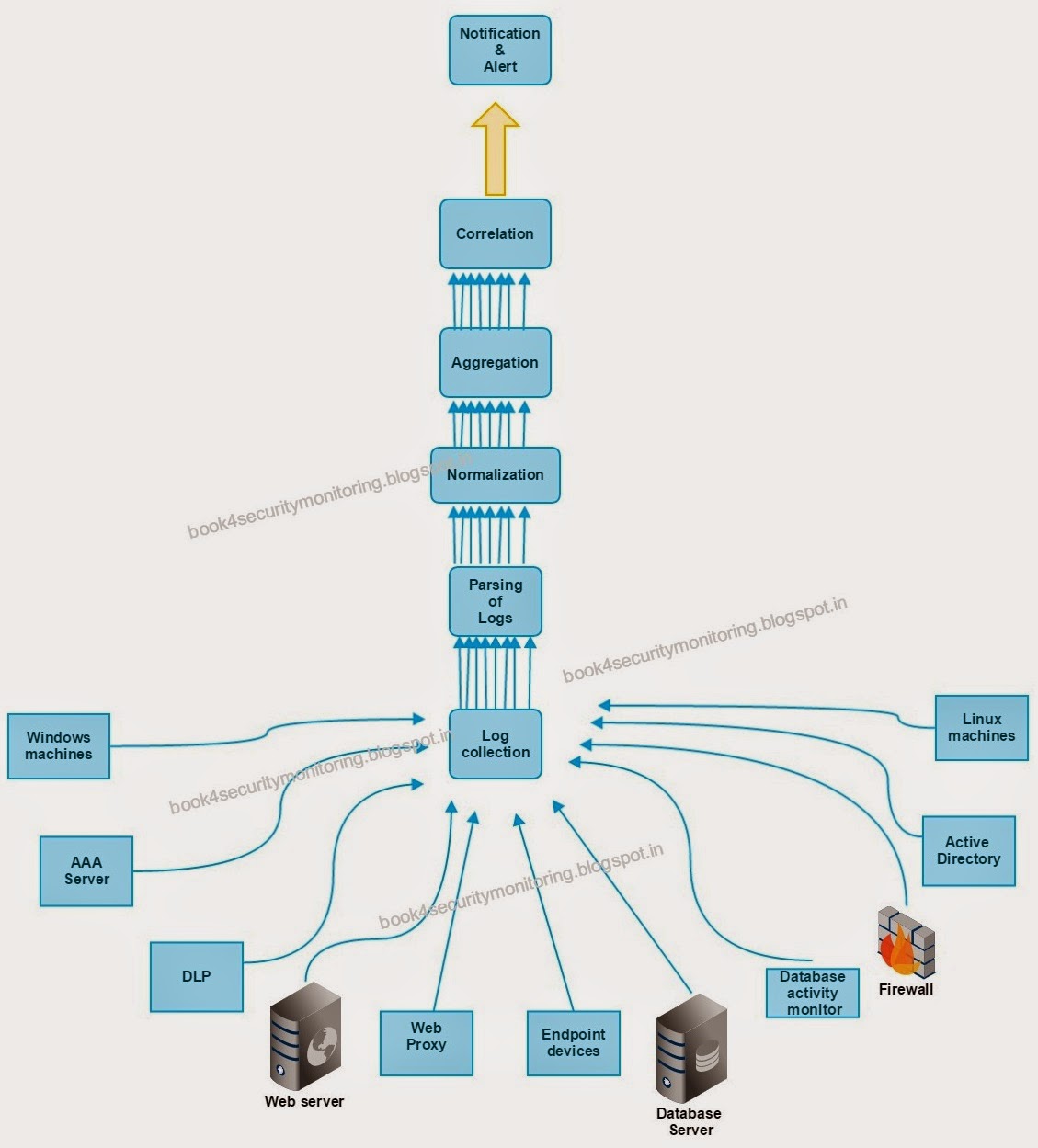
Security Monitoring Handbook for Secrity Analyst: Generalize

SIEM – A Beginner’s Guide What is a SIEM

Managed SIEM | CPTech.com

Elastic SIEM | Installer et configurer Elasticsearch et Kibana sur Debian

What is SIEM and Why is it so Important? - DevOpsSchool.com

Everything You Need to Know about SIEM Architecture

Overview of a SIEM architecture, showing some of the core facility

SIEM Architecture
